Emulate HTTPS Server
- 3 minutes to read
TestCafe Studio is a proxy-based testing tool. The TestCafe reverse proxy communicates with the original web server over HTTP or HTTPS (depending on the URL), but can only serve the page over HTTP (without extra configuration).
If your page uses SSL-only features like Service Workers, Geolocation API, ApplePaySession, or SubtleCrypto, configure the proxy server to use HTTPS. Continued use of HTTP would result in page loading issues, JavaScript errors, and, ultimately, test failure.
Note
If you test HTTPS-dependent Web features on a local machine in a Chromium-based browser or Firefox, we recommend that you first try a workaround that does not require an SSL connection. Specify localhost or 127.0.0.1 in the Hostname field in the Preferences/Settings Dialog. Chromium browsers and Firefox trust the localhost domain, so they enable most HTTPS-dependent features without SSL.
To enable HTTPS connections, open the Preferences/Settings Dialog and activate the Use SSL switch in the SSL Settings section.
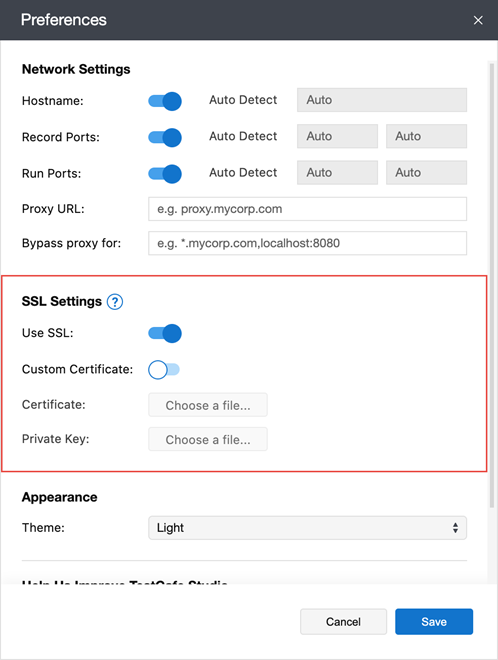
SSL Certificates
The TestCafe proxy server needs an SSL certificate to enable HTTPS. TestCafe Studio ships with a self-signed certificate that is safe to use in most testing environments. Alternatively, TestCafe Studio can use your self-signed or CA-signed trusted certificate to serve the tested page.
Use a Trusted Certificate
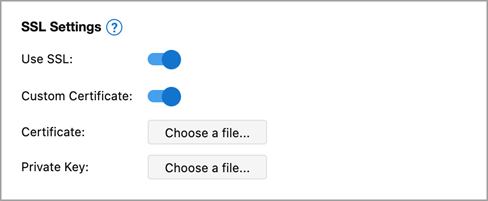
To use a certificate signed by a trusted authority, open the Preferences/Settings Dialog and enable the Custom Certificate switch in the SSL Settings section. Use the Certificate and Private Key fields to specify the certificate file and key.
Use a Self-Signed Certificate
To use TestCafe Studio’s self-signed certificate, open the Preferences/Settings Dialog and ensure the Custom Certificate switch is disabled in the SSL Settings section.
Alternatively, you can provide your own self-signed certificate. Enable Custom Certificate and use the Certificate and Private Key fields to specify your certificate file and key.

However, modern browsers do not trust self-signed certificates. You need to configure the browser to accept them.
Note
If your security policy allows, use a trusted certificate instead of self-signed. This permits the browsers to open the tested page without workarounds.
Chromium-based Browsers
A flag that configures Chromium to trust self-signed certificates is added automatically if you use the TestCafe Studio certificate (the Custom Certificate option is disabled).
When you use your own self-signed certificate, open the Run Configuration Dialog and add --ignore-certificate-errors to the browser’s command line arguments.
Note
When Hostname in the Preferences/Settings Dialog is set to localhost or 127.0.0.1, TestCafe Studio adds --allow-insecure-localhost instead of --ignore-certificate-errors for SSL connections.
Mozilla Firefox
Follow the steps below:
- Create a new profile in Firefox settings.
- Run Firefox with this profile and import the CA certificate that was used to verify the self-signed certificate. If you use the TestCafe Studio’s self-signed certificate, you can get the CA certificate here.
- Load this new profile when TestCafe Studio launches Firefox. To do this, add
-P <profile_name>to the browser’s command line arguments in the Run Configuration Dialog. Ensure that Load user profile is disabled (to avoid loading the most recent profile instead).
Warning
Use the Firefox profile configured to trust self-signed certificates for testing purposes only.
Other Browsers
The basic approach for other browsers is similar to Firefox’s.
Run the browser and import the CA certificate that was used to verify the self-signed certificate. If you use the TestCafe Studio’s self-signed certificate, you can get the CA certificate here.
Warning
We recommend that you use this approach only for browsers on dedicated testing virtual machines or testing farms for security reasons. Ensure you do not expose the private key during the process.
