Prevent Users from Deleting and Updating Administrative User and Role Objects
- 3 minutes to read
This topic explains how to create Validation and Conditional Appearance Rules to prevent users from deleting and updating administrative user and role objects. These rules affect all users including administrative users.
This help topic uses the XPO-based PermissionPolicyUser and PermissionPolicyRole classes. In applications based on EF 6 and EF Core, use the PermissionPolicyUser and PermissionPolicyRole classes from the DevExpress.Persistent.BaseImpl.EF.PermissionPolicy namespace.
Prevent Deletion of Administrative Users and Roles
- Add the Validation Module to the platform-agnostic Module.
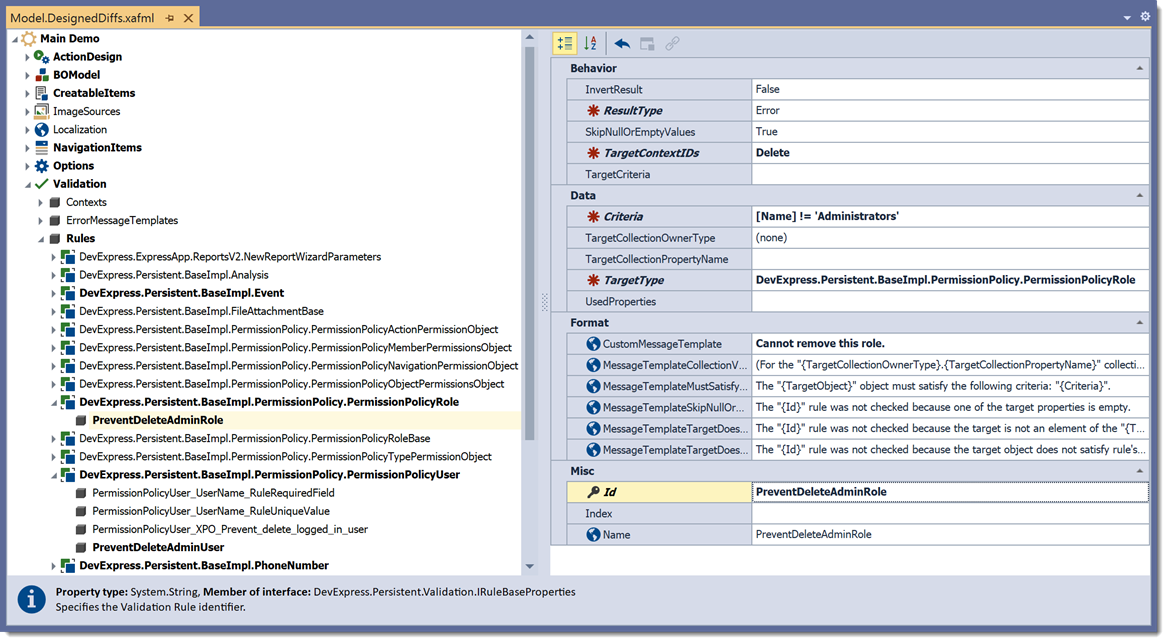
Open the Model Editor and navigate to the Application | Validation | Rules node. Right-click this node and add the following RuleCriteria that prevent deletion of the “Admin“ User and “Administrators“ Role:
Rule ID
TargetContextIDs
Criteria[1]
TargetType
CustomMessageTemplate
PreventDeleteAdminUser
Delete
[UserName] != ‘Admin’
PermissionPolicyUser
(or a custom user type)Cannot remove this user.
PreventDeleteAdminRole
Delete
[Name] != ‘Administrators’
PermissionPolicyRole
(or a custom role type)Cannot remove this role.
Alternatively, you can open the Model.DesignedDiffs.xafml file as an XML file and add the following elements:
<?xml version="1.0" encoding="utf-8"?> <Application> <!-- ... --> <Validation> <Rules> <!-- ... --> <RuleCriteria Id="PreventDeleteAdminUser" TargetContextIDs="Delete" Criteria="[UserName] != 'Admin'" TargetType="DevExpress.Persistent.BaseImpl.PermissionPolicy.PermissionPolicyUser" CustomMessageTemplate="Cannot remove this user." IsNewNode="True" /> <RuleCriteria Id="PreventDeleteAdminRole" TargetContextIDs="Delete" Criteria="[Name] != 'Administrators'" TargetType="DevExpress.Persistent.BaseImpl.PermissionPolicy.PermissionPolicyRole" CustomMessageTemplate="Cannot remove this role." IsNewNode="True" /> </Rules> </Validation> </Application>
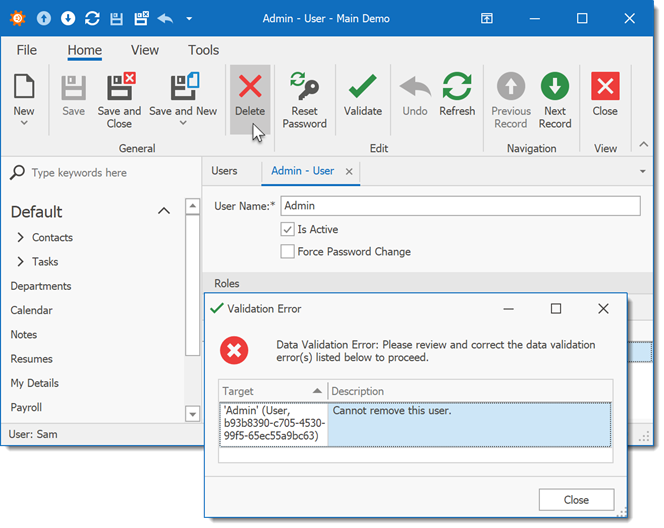
The following image shows the result:
Prevent Update of Administrative Users and Roles
- Add the Conditional Appearance Module to the platform-agnostic Module.
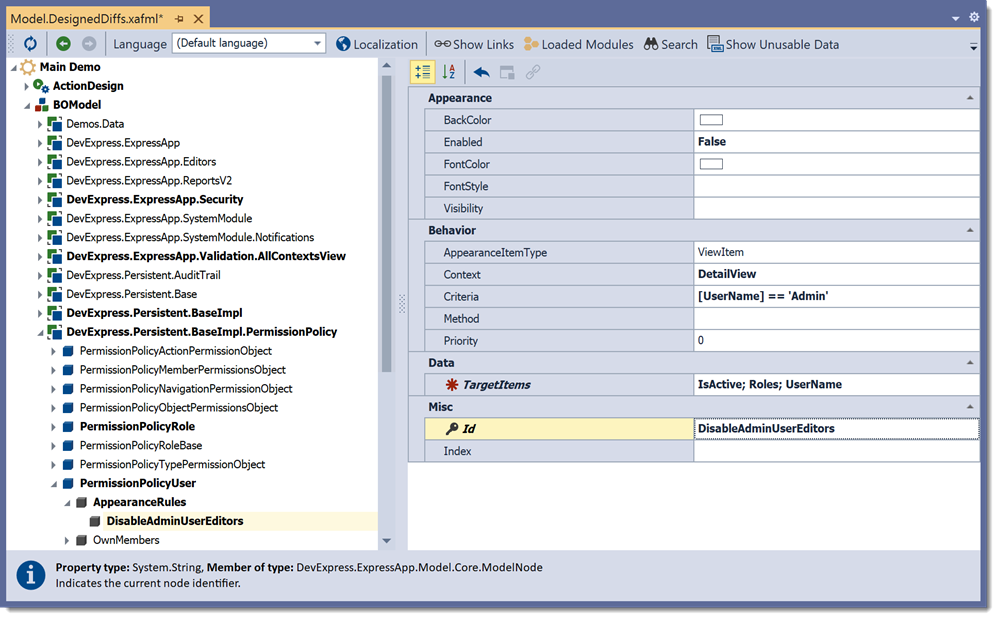
Open the Model Editor and navigate to the Application | BOModel | DevExpress.Persistent.BaseImpl.PermissionPolicy | PermissionPolicyUser | AppearanceRules node. Right-click this node and add the following rule that disables editors on the Detail View of the “Admin“ User:
ID
Enabled
Context
Criteria[1]
Target Items
DisableAdminUserEditors
False
DetailView
[UserName] == ‘Admin’
IsActive; Roles; UserName
Alternatively, you can open the Model.DesignedDiffs.xafml file as an XML file and add the following element:
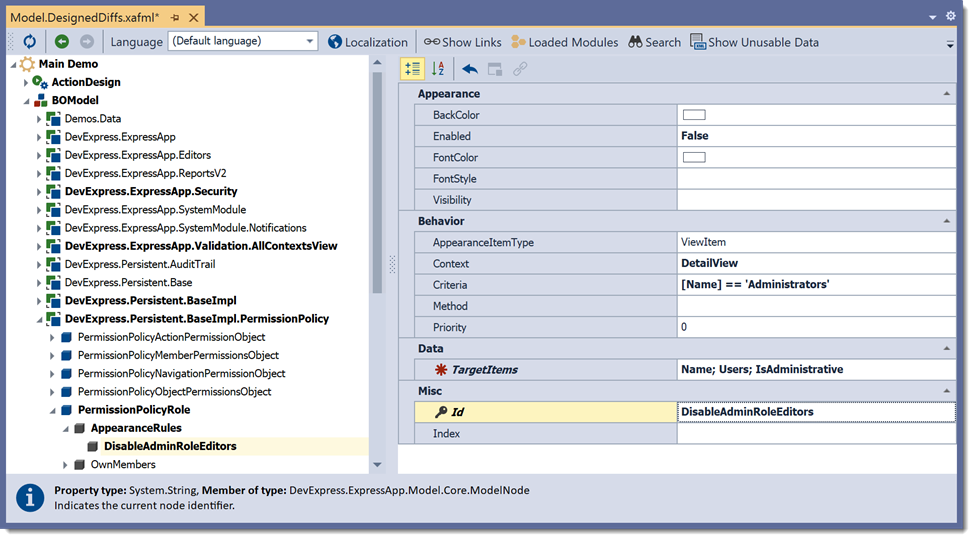
<?xml version="1.0" encoding="utf-8"?> <Application> <!-- ... --> <BOModel> <!-- ... --> <Class Name="DevExpress.Persistent.BaseImpl.PermissionPolicy.PermissionPolicyUser"> <AppearanceRules> <AppearanceRule Id="DisableAdminUserEditors" Enabled="False" Context="DetailView" Criteria="[UserName] == 'Admin'" TargetItems="IsActive; Roles; UserName" IsNewNode="True" /> </AppearanceRules> </Class> </BOModel> </Application>Open the Model Editor and navigate to the Application | BOModel | DevExpress.Persistent.BaseImpl.PermissionPolicy | PermissionPolicyRole | AppearanceRules node. Right-click this node and add the following rule that disables editors on the Detail View of the “Administrators“ Role:
ID
Enabled
Context
Criteria
Target Items
DisableAdminRoleEditors
False
DetailView
[Name] == ‘Administrators’
Name; Users; IsAdministrative
Alternatively, you can open the Model.DesignedDiffs.xafml file as an XML file and add the following element:
<?xml version="1.0" encoding="utf-8"?> <Application> <!-- ... --> <BOModel> <!-- ... --> <Class Name="DevExpress.Persistent.BaseImpl.PermissionPolicy.PermissionPolicyRole"> <AppearanceRules> <AppearanceRule Id="DisableAdminRoleEditors" Enabled="False" Context="DetailView" TargetItems="Name; Users; IsAdministrative" Criteria="[Name] == 'Administrators'" IsNewNode="True" /> </AppearanceRules> </Class> </BOModel> </Application>
The following image shows the result:
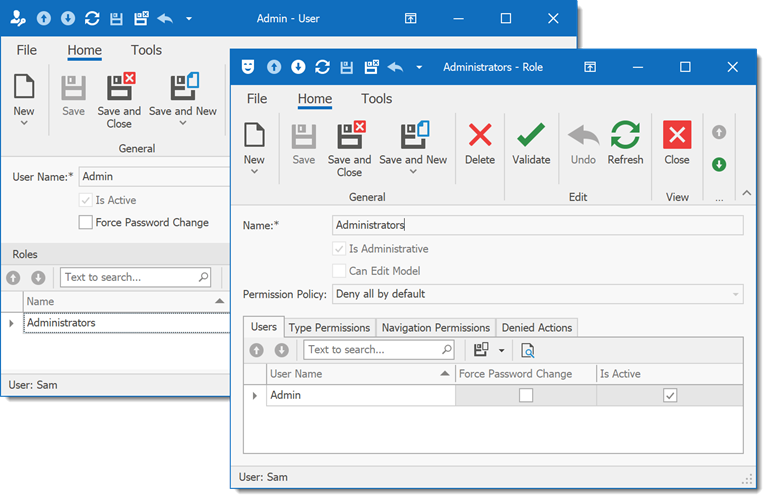
-
Note that users should have permission to read the PermissionPolicyUser.UserName and PermissionPolicyRole.Name properties. Otherwise, their values are replaced with the “*******“ placeholder and no object matches the specified criteria. Grant permission to read the UserName and Name properties or use Oid/Id instead in criteria (all users have permission to read this property).