Data Access Security
- 4 minutes to read
This document describes how to avoid possible security risks when reporting applications access data.
Important
The End-User Report Designer’s initial settings ensure a high level of database security.
We strongly recommend that you utilize the default settings if your reporting application can be accessed by untrusted parties.
We also recommend that you use the access control features of your database management system to achieve the highest level of database security.
SQL Data Sources
Consider the security measures listed below if your application connects to SQL data sources. Utilize the access control functionality of your database management system for the highest level of database security.
Enable Custom SQL Queries
The Data Source Wizard initially allows only SQL queries visually designed in the built-in Query Builder. The Query Builder can construct only SELECT queries that are safe.
Default security settings do not allow you to edit SQL query text directly. When you invoke the Data Source Wizard dialog, the text editor is disabled:

Enable SQL editing at your own risk as described in the following topic: Custom SQL Query in the Report Designer.
Validate Custom SQL Queries
Custom SQL queries are validated before their execution. Although the default validation mechanism only allows custom queries with SELECT statements (except for SELECT INTO clauses), they are not safe as they does not prevent execution of potentially harmful requests. You should implement secure SQL validation before you allow custom SQL queries.
To validate custom SQL for all queries created in your applications, handle the ValidateCustomSqlQueryGlobal static event.
Review the following topic for more information: Custom SQL Query Validation.
Entity Framework Data Sources
Loading of custom assemblies that may be referenced by Entity Framework data sources is forbidden by default. To allow users to select types from a custom assembly, handle the EFDataSource.BeforeLoadCustomAssembly event (or the static EFDataSource.BeforeLoadCustomAssemblyGlobal event) and specify the following properties of the BeforeLoadCustomAssemblyEventArgs object:
BeforeLoadCustomAssemblyEventArgs.AllowLoading
Specifies whether you can load a custom assembly.
BeforeLoadCustomAssemblyEventArgs.AssemblyPath
Specifies the path to the requested assembly.
BeforeLoadCustomAssemblyEventArgs.ContextName
Specifies the type to load from the assembly.
If an unauthorized attempt to load a custom assembly occurs, the CustomAssemblyLoadingProhibitedException exception is thrown.
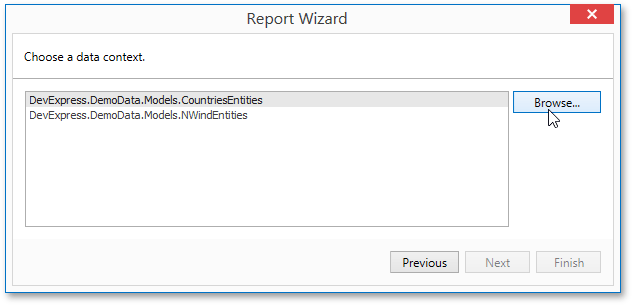
In the Entity Framework Data Source wizard, users can load custom assemblies when they hit the Browse button on the Select the Data Context page. In the End-User Designer, this button is hidden by default - users can only select the data context from assemblies referenced by the project.
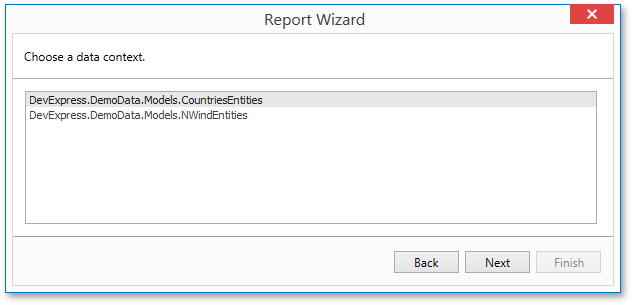
To enable the Browse button, set the EFWizardSettings.ShowBrowseButton property to true or assign a custom IWizardCustomizationService implementation to the ReportDesignerBase.ServicesRegistry property of a Report Designer.
The following example illustrates how to allow users to load a custom assembly to the Entity Framework context: Report Designer for WPF - How to enable end users to load custom assemblies to the Entity Framework context.
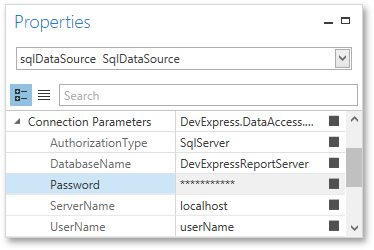
Protect Connection Password
In the End-User Report Designer for WPF, the password portion of the connection string is obscured with asterisk characters in the application’s GUI.
Restrict Access to External Resources
Ensure that reports from untrusted sources cannot use the DataSource or XmlDataPath property to access the file system and read files. Restrictions affect ExcelDataSource and JsonDataSource data sources.
You can use static properties and methods of the AccessSettings class to explicitly specify file operation restrictions for Excel data sources and specify allowed URLs for JSON data sources. If your application does not retrieve data from file-based data sources, add the DirectoryAccessRule.Deny() access rule to the AccessSettings.DataResources settings to prohibit all file operations with data sources (review the following code snippet for more information):
// JSON data can be loaded only from URLs; Excel data cannot be loaded from file directories (Excel data load from URLs is not supported)
bool success = DevExpress.Security.Resources.AccessSettings.DataResources.TrySetRules(
DevExpress.Security.Resources.UrlAccessRule.Allow(),
DevExpress.Security.Resources.DirectoryAccessRule.Deny()) ;
if (!success) System.Diagnostics.Debug.Print("Cannot change rules. The rules are already set.")