Data Access Security
- 5 minutes to read
This document describes how to ensure a secure access to data in your end-user reporting applications for Windows Forms and lists approaches allowing you to customize the default security mechanisms:
Important
Default data access behavior of the End-User Report Designer is intended to provide a high level of database security.
We strongly recommend that you utilize the default behavior if your reporting application can be accessed by untrusted parties.
We also recommend that you use the access control functionality of your database management system to achieve the highest level of database security.
SQL Data Sources
To enable your end-users to safely connect to SQL data sources without exposing your infrastructure to any risks, consider the following security issues.
Preventing SQL Injections
By default, the SQL Data Source wizard only allows the visual construction of SQL queries using the built-in Query Builder. Queries constructed using the Query Builder can only contain a SELECT statement and are guaranteed to be safe.
Manual editing of SQL queries is considered unsafe and is disabled by default. You can enable SQL editing at your own risk using the approach described in the Enable Custom SQL in Report Designer document.
If custom SQL editing is enabled, the Data Source wizard allows users to edit the SQL string text box contents located on its query creation page.
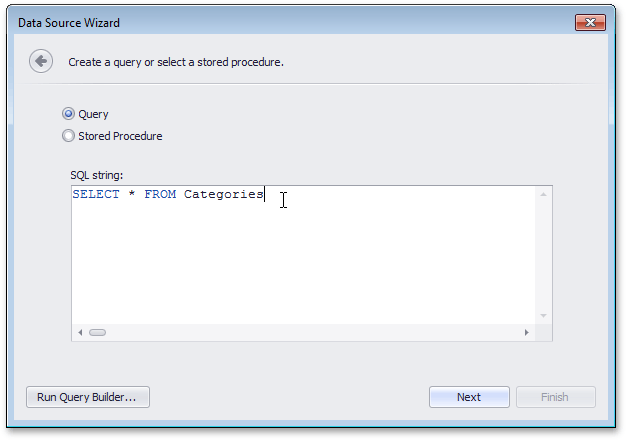
Important
Custom SQL queries are validated before their execution. Although the default validation mechanism only allows custom queries containing SELECT statements (except for SELECT INTO clauses), it cannot be considered safe as it does not prevent execution of potentially harmful requests. For this reason, we strongly recommend that you implement your own validation logic that permits only execution of specific query kinds. To learn more, see the Provide Custom Query Validation in Report Designer document.
Protecting Connection Information
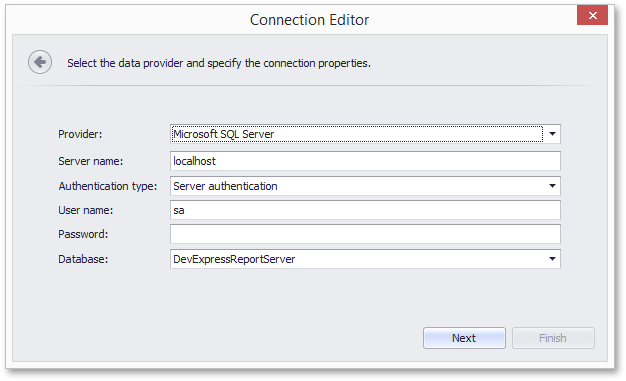
When connection strings are predefined and available in the Data Source wizard of the End-User Report Designer (e.g., by implementing the IConnectionStorageService interface), the password portion of the connection string is protected in the following ways.
When specifying the connection parameters of a specific data provider, the password is not displayed.
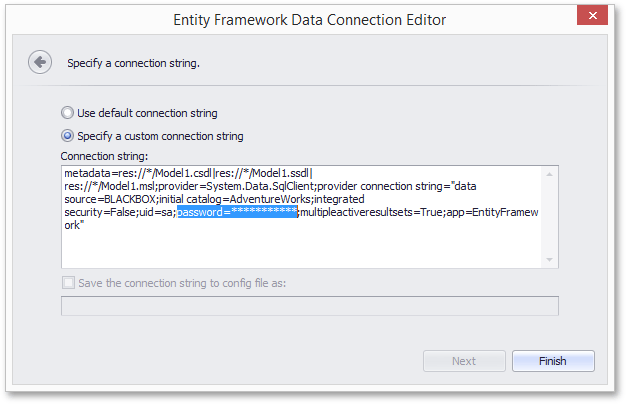
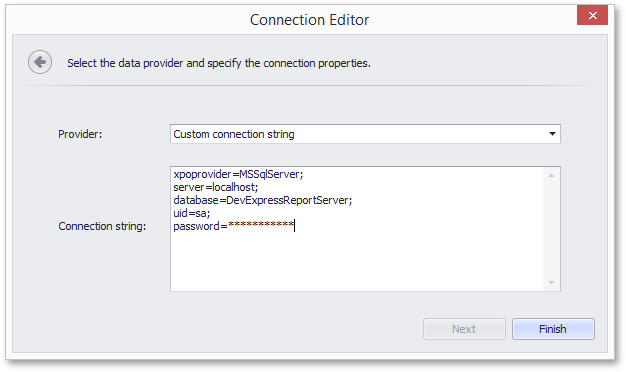
When specifying a custom connection string in the Data Source wizard, the password is obscured with asterisk characters (their number does not correspond to the actual length of the password).
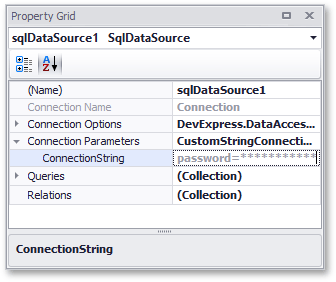
The same applies to the password portion when viewing a connection string information inside the Property Grid (when that data source component is selected in the Report Explorer).
If the connection string validation fails, the displayed error message will not reveal the password as well.
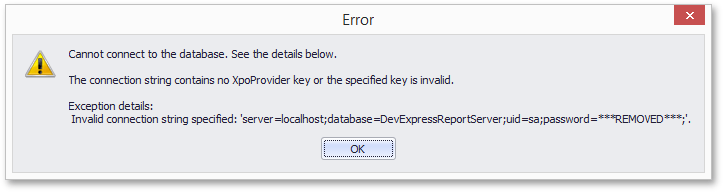
Serialization of Connection Parameters
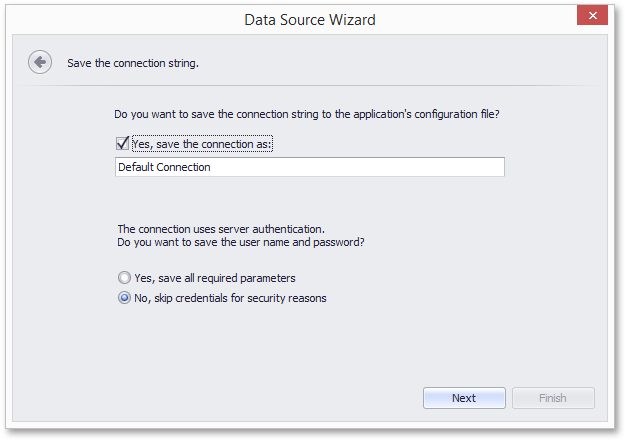
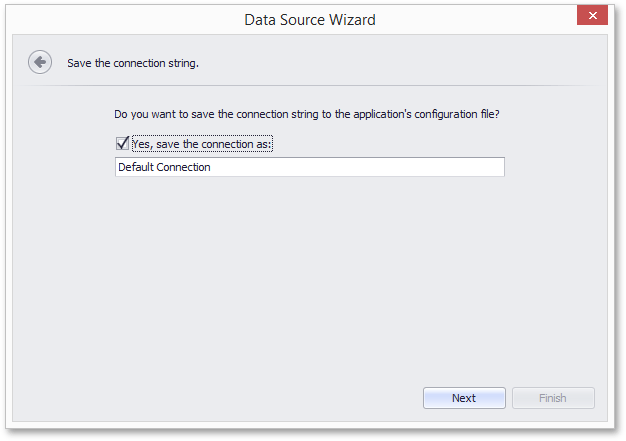
To always serialize only database connection names, set the DataConnectionBase.StoreConnectionNameOnly property to true. This will guarantee that the database credentials are never exposed in report layout definitions.
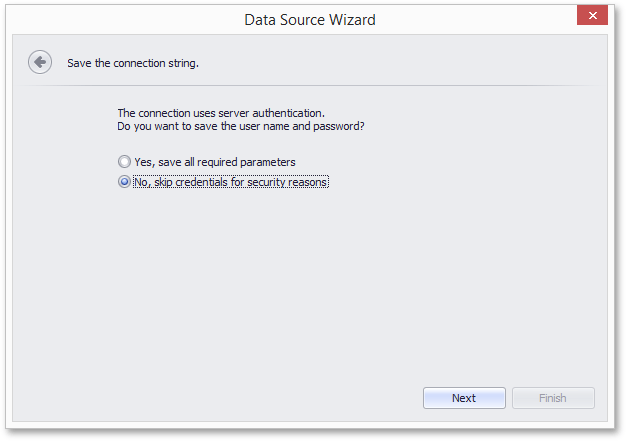
When this property is set to false (the default value), the resulting behavior depends on the settings defined for the SqlWizardSettings.DatabaseCredentialsSavingBehavior and IConnectionStorageService.CanSaveConnection properties.
Behavior | |
|---|---|
| |
SensitiveInfoSavingBehavior.Always or SensitiveInfoSavingBehavior.Never | End-users cannot specify whether or not the database credentials will be stored along with serialized layouts, which depends on the specified DatabaseCredentialsSavingBehavior setting. After an existing connection is selected (or a new one is specified), the Data Source wizard displays the following page.
|
Important
See Reporting Security for more information on security considerations related to storing and distributing DevExpress reports.
Entity Framework Data Sources
To enable your end-users to safely connect to Entity Framework data sources without exposing your infrastructure to any risks, consider the following security issues.
Restricting Access to Unauthorized Assemblies
Loading of custom assemblies that may be referenced by Entity Framework data sources is forbidden by default. To permit loading a specific assembly, handle the EFDataSource.BeforeLoadCustomAssembly event (or static EFDataSource.BeforeLoadCustomAssemblyGlobal event) and specify the following properties of the BeforeLoadCustomAssemblyEventArgs object.
BeforeLoadCustomAssemblyEventArgs.AllowLoading
Specifies whether loading a custom assembly is allowed.
BeforeLoadCustomAssemblyEventArgs.AssemblyPath
Specifies the path to a requested assembly.
BeforeLoadCustomAssemblyEventArgs.ContextName
Specifies the type to load from a custom assembly.
An unauthorized attempt to load a custom assembly will result in throwing a CustomAssemblyLoadingProhibitedException.
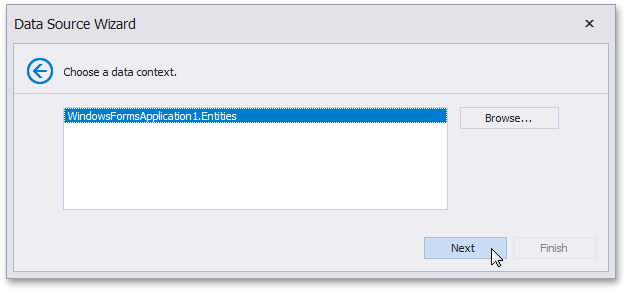
In the Entity Framework Data Source wizard, it is possible to load custom assemblies by using the Browse button on the Select the Data Context page. In the End-User Designer, this button is hidden by default, so that end-users are allowed only to select the data context from assemblies referenced by the project.
To make the Browse button visible, set the EFWizardSettings.ShowBrowseButton property to true.
Protecting Connection Information
In the End-User Report Designer, the password portion of the connection string is obscured with asterisk characters (their number does not correspond to the actual length of the password):
inside the Property Grid (when that data source component is selected);
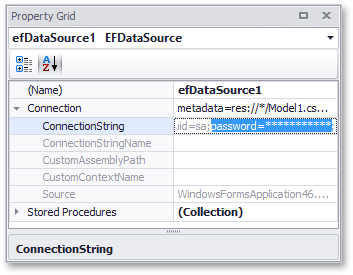
in the Data Source wizard (when modifying Entity Framework Data Source settings with a custom connection string).